When I'm building an image (especially a hardware independent image), the driver injection tends to be the hardest part - for obscure or old bits of hardware anyway.
I had a recent encounter with an old ATI Radeon X300 low profile graphics card. The image was to be built for Windows 8. The last drivers published were for Windows 7 and included in a legacy package from 2010!
I count myself lucky they had WDDM drivers for Windows 7 64-bit.
Problem
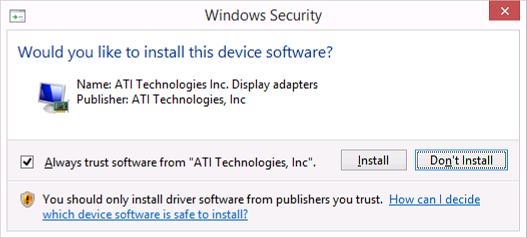
Refer to the dialog above. In this case, drivers were to be injected using pnputil.exe. During a sysprep'd startup, any application that blocks execution with a dialog is frustrating. This was a major hurdle.
Solution
After further investigation, I found that checking the 'Always trust software from '{vendor}' box actually imports a certificate into the Cert:\LocalMachine\TrustedPublisher store. On opening certlm.msc, I observed the following:
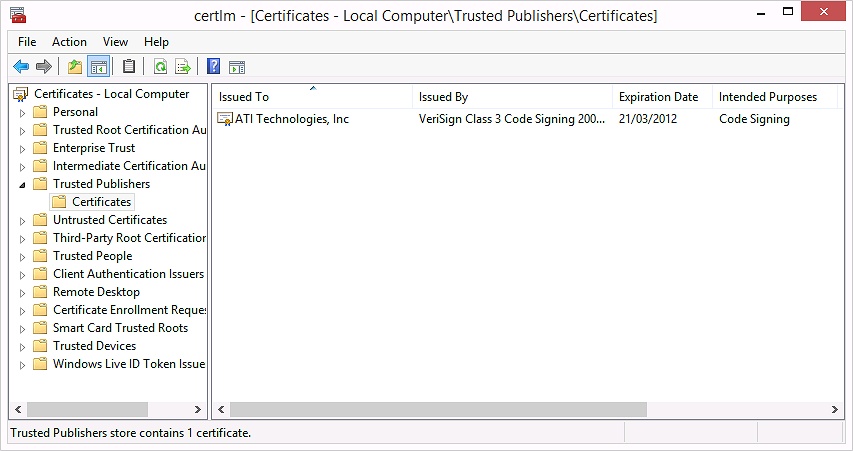
Pro tip: Export these certificates on a test machine. Programatically import the certificates before importing the drivers. Everything works perfectly!
The script is included below. It imports all certificates in C:\Drivers\Certificates and then imports all drivers in C:\Drivers\ sub-directories.
#
# Title: Install-Drivers.ps1
# Author: Jourdan Templeton
# Email: [email protected]
# Modified: 24/06/2014 11:49AM NZDT
#
$base_dir = "C:\Drivers"
$log_file = "C:\Logs\Install-Drivers.log"
Start-Transcript -Path $log_file -Append -NoClobber
Write-Output "[*] Importing Trusted Publishers..."
$certificates = Get-ChildItem -Path ($base_dir + "\Certificates") -Filter *.cer -Recurse
ForEach ($certificate in $certificates)
{
$cert = Import-Certificate -FilePath $certificate.FullName -CertStoreLocation Cert:\LocalMachine\TrustedPublisher
Write-Output $cert.Subject
}
Write-Output "`r`n[*] Importing Drivers..."
$drivers = Get-ChildItem -Path $base_dir -Filter *.inf -Recurse
ForEach ($driver in $drivers)
{
Write-Host $driver.FullName
pnputil.exe -i -a $driver.FullName
}
Stop-Transcript
Should read fairly easily - post below for help.
Jourdan